
Are you captivated by the hacking universe and aspire to transform your intrigue into a technical skill? Our blog post unravels the top ethical hacking courses ideal for mastering this sought-after ability. Whether you’re a cybersecurity novice eager to understand the basics or an advanced professional aiming to expand your expertise, this detailed guide assists you in selecting an ethical hacking course tailored to your requirements. Brace yourself for an exciting expedition towards becoming a proficient ethical hacker!
An Overview of Ethical Hacking
Ethical hacking, also known as penetration testing or white-hat hacking, is an authorized practice of bypassing system security to identify potential data breaches and threats in a network. The company that owns the system or network allows cybersecurity engineers to perform such activities to test the system’s defenses. Thus, unlike malicious hacking, this process is planned, approved, and, more importantly, legal.
Ethical hackers aim to investigate the system or network for weak points that malicious hackers can exploit or destroy. They collect and analyze the information to figure out ways to strengthen the security of the system/network. Numerous organizations globally recognize the value of ethical hacking and thus invest heavily in superior-quality ethical hacking courses to upskill their workforce.
The most popular ethical hacking courses available
There are several top-rated ethical hacking courses available to those eager to delve into the realm of cybersecurity. Here, we provide an overview of some of these courses.
- Certified Ethical Hacker (CEH): This is one of the most sought-after ethical hacking courses. Offered by the EC-Council, it covers over 340 attack technologies commonly used by hackers.
- Offensive Security Certified Professional (OSCP): Known as the “gold standard” in ethical hacking, this course is intense and practical. To earn certification, participants must successfully exploit a series of targets in a 24-hour exam.
- GIAC Penetration Tester (GPEN): This course focuses on conducting a penetration test and helps students understand how to scope a project and work thorough checks properly.
- Certified Intrusion Analyst (GCIA): This course teaches students how to use intrusion detection systems, and it covers network protocols, network intrusion detection, and traffic analysis.
- Certified Penetration Tester (CPT): Offered by IACRB, this course focuses on the five phases of penetration testing. The student will need to demonstrate proficiency in each stage to earn certification.
- Certified Expert Penetration Tester (CEPT): This course focuses on advanced penetration testing techniques and is also offered by IACRB, like the CPT. Students must have a clear understanding of exploits and vulnerabilities to succeed.
Dooey Ethical Hacker Certification Course

The EC-Council’s Certified Ethical Hacker (CEH) course, CEH 12, offers an immersive journey into cybersecurity. This contemporary, hands-on training program equips you to identify vulnerabilities, perform accurate threat analysis, and apply practical techniques. Each module presents real-world scenarios, allowing you to hone your skills in a secure virtual environment with the latest hardware and software tools.
Integrated practice tests aid your learning, preparing you for the final certification exam. The course keeps you updated with the newest exploit codes and offers mastery over hacking tools like Metasploit Framework and Kali Linux. As a certified professional, you’ll be adept at implementing security measures and thwarting cyber threats, paving the way for a thriving career.
Features of Dooey Ethical Hacker Certification Course
- Comprehensive Curriculum: The Dooey Ethical Hacker Certification Course delivers a wide-ranging curriculum covering all aspects of ethical hacking, ensuring you understand the subject deeply.
- Practical Experiences: The course offers hands-on experience through real-world scenarios that equip you with practical skills, preparing you to tackle cybersecurity challenges.
- Industry-Recognized Certification: Upon course completion, you receive a widely recognized certification, enhancing your credibility in the cybersecurity field.
- Latest Tools and Techniques: The course stays updated with the most recent exploit codes and provides mastery over hacking tools like Metasploit Framework and Kali Linux.
- Integrated Practice Tests: The course includes practice tests that aid learning and prepare you for the final certification exam.
- Expert-led Training: The training is led by industry experts, ensuring you receive high-quality instruction based on real-world experience and insights.
- Career Opportunities: Completion of the course opens doors to a vast range of career opportunities in the cybersecurity domain.
Pros & cons of Dooey Ethical Hacker Certification Course
Pros:
- Comprehensive curriculum covering all aspects of ethical hacking
- Hands-on experience through real-world scenarios
- Widely recognized certification upon completion
- Up-to-date with the latest tools and techniques
- Includes practice tests to aid learning and prepare for the final exam
- Expert-led training from industry professionals
- It opens doors to a wide range of career opportunities
Cons:
- Course fees may be expensive for some individuals
- Requires a certain level of technical proficiency and understanding of computer systems
- Requires dedication and continuous learning to keep up with evolving cyber threats.
The Bottom Line
With the increasing number of cyber threats, ethical hacking has become a crucial aspect of cybersecurity. Choosing the right ethical hacking course is essential to gain the necessary skills and knowledge. The Dooey Ethical Hacker Certification Course offers a comprehensive curriculum, practical experience, and industry-recognized certification, making it one of the best ethical hacking courses available. With expert-led training and up-to-date tools and techniques, this course equips you for a successful career in cybersecurity.
CyberVista Certified Ethical Hacker Training Course

Our comprehensive prep course is designed to fully equip you for the CEH exam, covering critical areas like footprinting, Reconnaissance, network scanning, system hacking, sniffing, and server hacking. As an online, on-demand course, it allows for flexible, self-paced learning from any location. Knowledge absorption is seamless with engaging video lessons from a certified instructor and the ability to rewatch sessions.
The course includes valuable resources such as guides and books for further text-based learning. Our practical labs offer hands-on scenario-based tasks for real-world preparation, making this course a complete learning package.
Features of Kaplan Certified Ethical Hacker Training Course (CyberVista)
- Comprehensive Exam Preparation: The course prepares you for the CEH exam by covering all critical areas of ethical hacking.
- Flexible Learning Options: As an online, on-demand course, you can learn at your own pace from any location.
- Engaging Video Lessons: Certified instructors deliver engaging video lessons, ensuring easy comprehension and knowledge retention.
- Access to Study Resources: The course includes valuable resources such as guides and books for further text-based learning.
- Hands-on Practice Labs: Practical labs offer hands-on scenario-based tasks for real-world preparation, making the course a complete learning package.
Pros & cons of Kaplan Certified Ethical Hacker Training Course (CyberVista)
Pros:
- Comprehensive exam preparation covering all critical areas
- Flexible learning options with on-demand access from any location
- Engaging video lessons from certified instructors
- Access to study resources for further text-based learning
- Hands-on practice labs for real-world preparation
Cons:
- Course fees may be expensive for some individuals
- Requires a certain level of technical proficiency and understanding of computer systems
- Limited access to instructors for personalized guidance and support
The Bottom Line
The Kaplan Certified Ethical Hacker Training Course (CyberVista) is an excellent option for those seeking comprehensive exam preparation. Its flexible learning options, engaging video lessons, and hands-on practice labs make it a complete learning package. However, the course may be more suitable for individuals with a certain level of technical proficiency and understanding of computer systems. With dedication and effort, this course can prepare you for the CEH exam and a successful career in ethical hacking.
EC-Council Certified Ethical Hacker (CEH) Certification Training
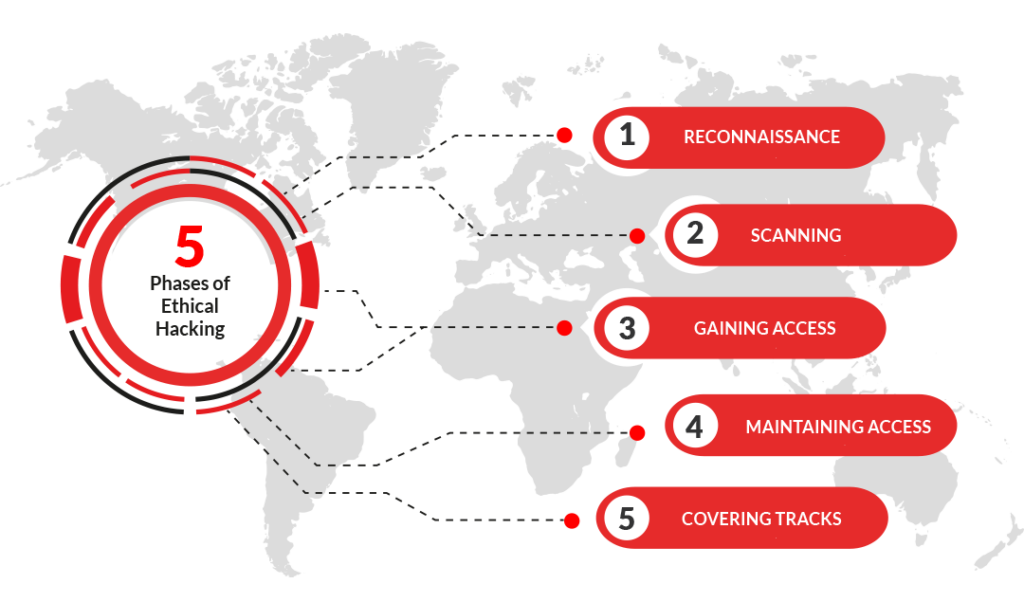
The EC-Council Certified Ethical Hacker (CEH) Certification Training course is designed to equip individuals with the necessary skills and knowledge to become successful ethical hackers. It covers many topics, including footprinting, network scanning, system hacking, and social engineering.
The course aims to provide hands-on experience through real-world scenarios and offers practical labs for further practice. With flexible learning options and expert-led training, this course is popular for those looking to become certified ethical hackers.
Features of EC-Council Certified Ethical Hacker (CEH) Certification Training
- Comprehensive Curriculum: The course covers many topics, providing a thorough understanding of ethical hacking.
- Hands-on Experience: Real-world scenarios and practical labs offer hands-on experience to enhance learning.
- Flexible Learning Options: The course offers flexible learning options, including on-demand access and in-person training.
- Expert-Led Training: Industry professionals provide expert-led training to understand concepts and techniques better.
- Preparation for Certification: The course prepares individuals for the CEH exam, leading to an industry-recognized certification.
Pros & cons of EC-Council Certified Ethical Hacker (CEH) Certification Training
Pros:
- Comprehensive curriculum covering a wide range of topics
- Hands-on experience through real-world scenarios and practical labs
- Flexible learning options, including on-demand access and in-person training
- Expert-led training from industry professionals for better understanding
- Preparation for the CEH exam and industry-recognized certification
Cons:
- Course fees may be expensive for some individuals
- Requires a basic understanding of computer systems and networks
- Limited access to instructors for personalized guidance and support
The Bottom Line
The EC-Council Certified Ethical Hacker (CEH) Certification Training course is an excellent choice for those looking to become certified ethical hackers. Its comprehensive curriculum, hands-on experience, and flexible learning options make it popular among individuals seeking a career in ethical hacking.
Dooey Ethical Hacker Certification Course vs Kaplan Certified Ethical Hacker Training Course (CyberVista)
The Dooey Ethical Hacker Certification Course and Kaplan Certified Ethical Hacker Training Course (CyberVista) are two remarkable contenders in ethical hacking education. The Dooey course distinguishes itself with its comprehensive curriculum, flexible learning options, and various topics, including hands-on practical labs for real-world scenarios.
On the other hand, Kaplan’s CyberVista course is notable for its in-depth exam preparation, engaging video lessons from certified instructors, and access to valuable study resources. However, both courses may be pricey for some individuals and require a basic understanding of computer systems. The choice between these two courses ultimately concerns personal preferences and learning style.
Tips For Finding the Best Ethical Hacking Course
When selecting the best ethical hacker course, take into consideration the following key aspects:
Course Content: The curriculum should comprehensively cover primary areas, including intrusion detection, DDoS attacks, buffer overflows, and virus creation. Make sure the content is holistic and thorough.
Industry Recognition: opt for courses acknowledged and endorsed by prominent IT and cybersecurity organizations. This recognition adds significant value to the system.
Practical Labs: Hands-on experience is crucial in understanding ethical hacking. Ensure the course provides ample opportunities for practical learning through labs.
Instructor Expertise: The instructors should have substantial knowledge and considerable professional experience in hacking and teaching. Their qualifications can significantly impact your learning experience.
Course Reviews and Ratings: Previous students’ feedback can provide essential insights into the course quality. Check the course ratings and reviews before making a decision.
Flexibility and Support: Consider the course’s flexibility in learning modes, time commitment, and support provided by the course provider. A good balance between self-paced learning and instructor-led sessions is ideal. Additionally, look for courses that offer job assistance or mentorship programs.
Analyzing Digital Footprints
A crucial aspect of ethical hacking is the analysis of digital footprints, the trail of data created during online interactions. These footprints can take various forms, like browsing history, social media activities, server logs, and data residing in cloud storage.
Each online action leaves a mark, and these marks, if examined meticulously, can uncover potential security vulnerabilities. A premium ethical hacking course will impart the skills needed to master this analysis, highlighting the steps to identify risks and devise strategies for their mitigation.
The best practices delve into understanding IP tracing, email tracking, and social media profiling, thus equipping students with the ability to decode these footprints and predict potential security threats. This knowledge helps fortify an organization’s cyber defenses by anticipating and addressing possible vulnerabilities.
Exploring Different Types of Hacking Techniques
Ethical hackers must immerse themselves in a wide array of hacking techniques. This understanding allows them to efficiently mimic a variety of cyber threats, reinforcing their organization’s security measures. Let’s look at some fundamental hacking strategies:
Password Cracking: A powerful tool for any hacker, it involves deciphering passwords from data stored or transmitted within computer systems. High-quality, ethical hacking courses highlight diverse password-cracking techniques, including dictionary attacks, brute force attacks, and rainbow table attacks.
Phishing: This tactic involves sending deceptive emails, text messages, or websites, tricking users into disclosing sensitive information. Learning to recognize and avert phishing attacks is essential to ethical hacking education.
SQL Injection: In this technique, a hacker exploits a security loophole in a database layer of an application. They feed malevolent SQL code into a query, allowing them to alter or disclose data.
Cross-Site Scripting (XSS): This technique occurs when an attacker introduces harmful scripts into credible websites. XSS allows the attacker to circumvent access controls and impersonate a genuine user.
Denial-of-Service (DoS) Attacks: This technique involves an attacker flooding a network, service, or server with excessive traffic to deplete resources and bandwidth, rendering the service inaccessible.
Peerless ethical hacking courses will cover these techniques, enabling you to comprehend the hacker’s mentality and safeguard your organization’s digital assets.
Gathering information about a target system or network
Information gathering, known as Reconnaissance, is a crucial step in ethical hacking. It involves collecting as much data as possible about the target system or network to identify potential vulnerabilities. This can be done through a variety of methods:
Active Reconnaissance: In this method, the hacker directly interacts with the target system to gather information. Examples include port scanning or initiating a direct connection to the system.
Passive Reconnaissance involves collecting data without directly interacting with the target system. Techniques include observing network traffic, utilizing search engines, public records, or social engineering.
Essential information to be gathered includes network structure, operating systems, IP addresses, usernames and passwords, installed applications, and firewall configurations. This data can then be analyzed to identify weak points and plan the most effective attack strategy. It’s important to emphasize that all these activities should be performed ethically and only with proper authorization.
Identifying and mapping network infrastructure
Identifying and mapping network infrastructure is vital to the ethical hacking process, providing a comprehensive overview of interconnected systems. This phase involves a detailed analysis of the network topology, including servers, routers, switches, gateways, and other network devices. Conducting a network enumeration can reveal specific details, such as hostnames, network shares, IP addresses, and user accounts.
Tools such as Nmap, Nessus, or Wireshark can be instrumental in discovering live hosts, open ports, and services running on the network. It’s a meticulous process that combines automated scanning with manual techniques to ensure a detailed mapping.
As with any other ethical hacking activity, having the necessary permissions before carrying out these tasks is crucial to avoid legal complications.
Extracting information about network users, resources, and devices.
Extracting information about network users, resources, and devices is another critical phase in ethical hacking. This procedure, often called data enumeration, involves identifying user accounts, system data, network resources, and other pertinent details.
Various tools like NetBIOS Enumeration Utility, User2SID, and SuperScan can gather user account details. At the same time, utilities like SNMP sweepers and Network View can disclose information about network devices and resources.
It’s important to note that while this process provides valuable insights, it could potentially infringe on privacy rights if misused. Therefore, as an ethical hacker, gaining authorization from the network owners before proceeding and handling the gathered data responsibly is essential.
Identifying and assessing vulnerabilities in systems and networks.
Identifying and assessing vulnerabilities in systems and networks is a crucial step in the ethical hacking process. This phase, often called vulnerability assessment, involves the systematic identification, quantification, and prioritization of vulnerabilities in a system. This is done using various tools and techniques, including vulnerability scanners like Nessus or OpenVAS, which automate checking systems for known vulnerabilities.
Similarly, manual techniques like code reviews and penetration testing can help identify potential security gaps. The information collected allows an ethical hacker to understand where security may be compromised and formulate strategies to strengthen it.
The ultimate goal is to mitigate risks, improve software and system security, and ensure that any potential attacks can be effectively counteracted. As with all ethical hacking activities, conducting these assessments only with proper authorization is essential to ensure legality and respect for privacy.
Gaining unauthorized access to systems.
Gaining unauthorized access to systems, often termed ‘system hacking,’ is the stage where the ethical hacker tries to break into the system using the vulnerabilities identified in the previous stages. This could involve password cracking, privilege escalation, executing applications, or exploiting known vulnerabilities.
Software tools like John the Ripper, Hydra, or Metasploit can be employed in this phase. Notably, this unauthorized access intends not to harm or steal data but to identify weak spots in the system’s security that need strengthening. It is an integral part of the ethical hacking process, enabling stakeholders to understand their systems’ security flaws.
The ethical hacker will typically document all steps taken during this stage to provide clear evidence and guidance for strengthening the system’s security. As always, this hacking stage should be conducted ethically and only with proper and explicit permissions.
Different areas of Ethical Hacking that you should be aware of
Several spheres within ethical hacking are vital to comprehend and master.
Web Application Hacking: In this field, ethical hackers focus on vulnerabilities in web applications, including injection flaws, cross-site scripting, and broken authentication.
System Hacking: This involves identifying weaknesses in system security to gain unauthorized access, extract sensitive data, or disrupt operations. Proficiency in operating systems like Linux, Unix, and Windows is needed.
Network Hacking: Here, the ethical hacker is tasked with securing network infrastructure by identifying vulnerabilities, preventing unauthorized access, and safeguarding data transmission.
Social Engineering: This human-centered attack vector involves manipulating individuals to divulge confidential information. Ethical hackers must understand human psychology to counteract these tactics effectively.
Wireless Network Hacking: As wireless networks increase, so does their vulnerability. This area pertains to securing wireless networks against unauthorized access and data theft.
Cryptanalysis: This study analyzes information systems to breach cryptographic security systems. Ethical hackers aim to uncover vulnerabilities and strengthen encryption protocols.
Malware Analysis: Ethical hackers must understand different types of malware, like viruses, worms, trojans, and ransomware, and how to defend systems against them.
Cloud Hacking: With the increasing shift towards cloud computing, securing cloud-based platforms has become a crucial aspect of ethical hacking. This involves securing data storage, databases, servers, and applications hosted in the cloud.
IoT Hacking: The Internet of Things (IoT) brings new challenges for ethical hackers. This involves securing IoT devices against threats and ensuring data privacy.
Penetration Testing: This is a crucial aspect of ethical hacking, which involves testing a system, network, or Web application to find vulnerabilities that an attacker could exploit.
Exploring Real-World Scenarios with Hands-On Practice Challenges
In the realm of ethical hacking, practical experience is paramount. Hands-on practice challenges provide the opportunity to apply learned theories in real-world scenarios, thus bridging the gap between theoretical knowledge and used skills. These challenges simulate various cyberattack scenarios, enabling learners to understand the threats better and devise appropriate countermeasures.
For instance, learners could be tasked to infiltrate a simulated network system, mimicking an actual cyberattack. The objective would be to identify and exploit vulnerabilities, similar to what a malicious hacker would do. Subsequently, they must document their findings and suggest improvements to bolster the system’s defense.
Different courses offer varying levels of practical challenges, from beginner-friendly tasks to complex projects that require learners to utilize multiple skills simultaneously. These real-world simulations not only enhance technical proficiency but also foster critical thinking and problem-solving abilities — key competencies in the cybersecurity field.
Therefore, when choosing the best ethical hacking course, consider the extent and quality of hands-on practice challenges they provide. A lesson with robust, practical components will prepare you to handle real-life cybersecurity incidents more effectively, making you a valuable asset in the ever-evolving digital landscape.
Learning How to Use Ethical Hacking Tools and Software
To become a proficient ethical hacker, you must familiarize yourself with various hacking tools and software. The best ethical hacking course will provide comprehensive training on such devices, enabling you to effectively detect vulnerabilities and secure your organization’s network. Here are some commonly used ethical hacking tools:
Wireshark: This open-source protocol analyzer allows you to examine your network at a microscopic level. Wireshark is used for network troubleshooting, analysis, software, and protocol development.
Metasploit: A vital tool for penetration testing, Metasploit allows ethical hackers to discover, validate, and manage security assessments. It’s a powerful tool for identifying vulnerabilities within the network.
Nmap: Commonly known as Network Mapper, Nmap is used for network discovery and security auditing. It can identify hosts and services on a network, generating a “map” of the system.
Burp Suite: This web server security tools application testing tool allows you to identify vulnerabilities and security holes in your web applications.
SQL map: An open-source penetration testing tool, SQL map automates detecting and exploiting SQL injection flaws and taking over the database servers.
John the Ripper: A popular password-cracking tool, it detects weak passwords. It combines several cracking modes and is fully configurable for your specific needs.
Kali Linux various is an open-source, Debian-based distribution for advanced Penetration Testing and Security Auditing. It includes hundreds of tools tailored for multiple information security tasks.
Nessus: It’s a remote security scanning tool that scans a computer and raises an alert if it discovers any vulnerabilities that malicious hackers could use to access any computer you have connected to a network.
Developing Your Security Strategies and Policies
Crafting Effective Security Strategies in Ethical Hacking
Creating effective security strategies is a fundamental aspect of ethical hacking and cybersecurity. The foremost ethical hacking courses expound not only on hacking techniques and tools but also underscore the criticality of robust strategies.
An effective process starts with a thorough risk assessment, pinpointing vulnerabilities susceptible to hacker exploitation. This entails monitoring and auditing systems to ensure swift detection and response to strange activities.
The best ethical hacking course will delve into these facets, teaching you how to predict vulnerabilities and develop counteractive strategies.
The Role of Policies in Ethical Hacking
Concomitant to strategies, policies are a structural framework guiding an organization’s response to potential security threats. True to their multi-faceted nature, they encapsulate different aspects, including incident response, user access control, and data backup and recovery.
Comprehending the significance of these policies and their correct implementation is pivotal in maintaining a secure digital environment. Inclusive, ethical hacking courses will teach how to define, apply, and manage these policies effectively, fostering a fortified defense mechanism.
Continual Adaptation of Strategies and Policies in Ethical Hacking
In the ever-evolving cybersecurity landscape, the threats and vulnerabilities are continually changing. This necessitates constantly updating and revising security strategies and policies to stay abreast of new threats.
Therefore, a significant aspect of the best ethical hacking course would include teaching how to effectively adapt, create, and update security strategies and policies. This ensures that the defenses are robust and agile, capable of combating emerging cyber threats.
The Benefits of Taking an Ethical Hacking Course
Comprehensive Understanding through the Best Ethical Hacking Course
Opting for the best ethical hacking course opens the gateway to a profound understanding of the complex concepts, tools, and techniques instrumental in ethical hacking. These courses instill deep cybersecurity knowledge, empowering you to identify system vulnerabilities accurately and develop effective risk mitigation strategies.
This practice ultimately sharpens your problem-solving skills, making you a valuable asset in the cybersecurity landscape.
Gaining Valuable Experience Through Practical Application
The best ethical hacking courses are theory-intensive and emphasize practical learning. They typically incorporate hands-on labs and real-world projects into the curriculum. Such experiences allow you to apply the theoretical knowledge gained, fostering your understanding of practical scenarios. This approach elevates your learning experience and ensures you are well-prepared to tackle real-world cybersecurity issues.
Validating Skills with Recognized Certifications
Another benefit of taking the best free ethical hacking course is validating your skills and knowledge through industry-recognized certifications. Certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or GIAC Certified Penetration Tester (GPEN) stand as a testament to your competency in the field.
This gives you a competitive edge in the job market with advanced Google hacking techniques, demonstrating to potential employers that you possess the skills and knowledge they seek.
Paving the Way for Lucrative Job Opportunities
Lastly, but most importantly, the best ethical hacking course acts as a stepping-stone toward lucrative career prospects. The escalation of digital threats has increased the demand for honest hacking professionals across various sectors.
With the credentials obtained from a top-rated ethical hacking course, you become a highly sought-after professional, opening up a world of opportunities in the cybersecurity realm.
Advice on How To Make the Most of Your Time in an Ethical Hacking Course
Making the most of your time in an ethical hacking legal can significantly enhance your learning experience and outcomes. Here’s how you can do it:
Engage Actively: Active participation is vital to absorbing course content and gaining a profound understanding. Engage with the instructors, ask questions, and participate in discussions to clarify doubts and enhance your knowledge.
Make Full Use of Practical Labs: Hands-on labs are crucial for understanding the practical aspects of ethical hacking. Ensure you are making the most out of these sessions. Apply the theories learned, experiment with different approaches, and don’t be afraid to make mistakes.
network security with Peers: Your peers are a valuable resource for learning. Collaborating with them on projects, sharing insights, and tackling problems can enrich your learning experience.
Take Advantage of Mentorship: If your course offers mentorship programs, utilize them fully. Mentors can provide guidance, industry insights, and helpful feedback on your progress.
Prepare for Certification Exams: While learning, simultaneously prepare for certification exams like CEH, OSCP, or GPEN. This approach consolidates your knowledge and prepares you for the rigorous examination process.
FAQs
How long does it take to complete an ethical hacking course?
The duration of an ethical hacking course may vary depending on the intensity and depth of the curriculum. However, most courses range from 40 to 60 hours in total. Some systems also offer flexible learning options, allowing students to complete the course at their own pace.
What are the prerequisites for taking an ethical hacking course?
There are no specific prerequisites for taking ethical hacking skills. However, having a basic understanding of networking and operating systems can be beneficial. Additionally, a passion for cybersecurity and problem-solving skills can aid in grass.
Are there any prerequisites for taking an ethical hacking course?
It is recommended to have a basic understanding of networking, operating systems, and programming languages. Some courses may also require prior knowledge of specific tools or concepts.
Can I take an ethical hacking course online?
Many reputable, ethical hacking training offer online learning options for added flexibility. However, ensuring that the course provider is credible and provides adequate support during the learning process is essential.
Is it necessary to have a computer science or cybersecurity background to take an ethical hacking course?
No, a computer science or cybersecurity background is not required to take a learn ethical hacking course. However, having some prior knowledge in these fields can be beneficial and facilitate the learning process.
Conclusion
I hope this document has highlighted the benefits of taking a top-rated ethical hacking course. From gaining practical experience to validating skills with recognized certifications and paving the way for lucrative job opportunities, such practices offer many advantages. Additionally, individuals can make the most of their time in an ethical hacking course by actively engaging in the learning process, using practical labs and mentorship programs, networking with peers, and preparing for certification exams.



